Problem description
If you have ordered a service which includes a GNU/Linux operating system, the first thing to be of interest to you may be where do you find the password for the root user.
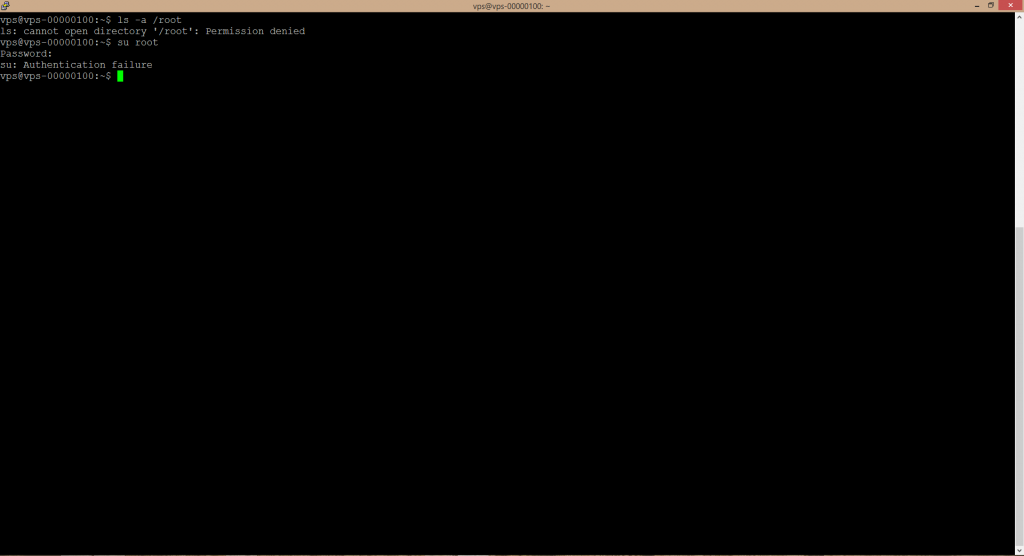
Especially when working in the terminal or more precisely in bash, you may encounter the situation when you want to execute a command, but the terminal responds with information regarding insufficient permissions, e.g. „Permission denied,“ etc. Or in case, you want to switch to the root user. The system will ask for the root user password. But you do not know it.
Maybe you have read in some of our service descriptions that you will receive the root access. Nevertheless, the root user account password was neither sent nor told you. The following text should clarify the reasons.
The reason for you not to know the root password
Neither our whim nor reluctance is the reason why we have not sent you the root account password. In fact, the reasons are historical and are closely related to security.
Within the operating system, it is possible to perform some operations, which can significantly affect its functionality or may even lead to its total collapse. Therefore, such operations are available within the operating system only for the users with appropriate permissions. These users are called „superusers, “ and the root user is exactly the example of the superuser.
However, there were and still are experiences with the use of superuser user accounts of such kind, where the users do use it to a much larger extent than they should, that is not only in order to perform operations for which it is necessary but also when performing common operations. Also, it is easy to forget that we work under the superuser account and so may possibly cause significant damage. Moreover, in the GNU/Linux operating systems, the root user account is the supreme user account, which potentially makes it the worst security threat at the same time.
These are the reasons why nobody had told you the root account password and never will do so. In fact, for the sake of achieving a higher level of security, the creators of the Linux distributions had decided that by default, the root user account password ought not to be defined. Now, you may ask, how is it possible to perform any operation which requires elevated permissions? The sudo mechanism, which was integrated into the operating system by the creators of the Linux distributions, is the answer to that.
The sudo mechanism
In simple words, „sudo“ is the group of the users, who are allowed to perform commands which require the elevated permissions. In other words, the users who are members of the sudo group do not need to use the root user account in order to perform commands requiring elevated permissions at all. Instead, they put the sudo command before the command they wish to perform, e. g.:
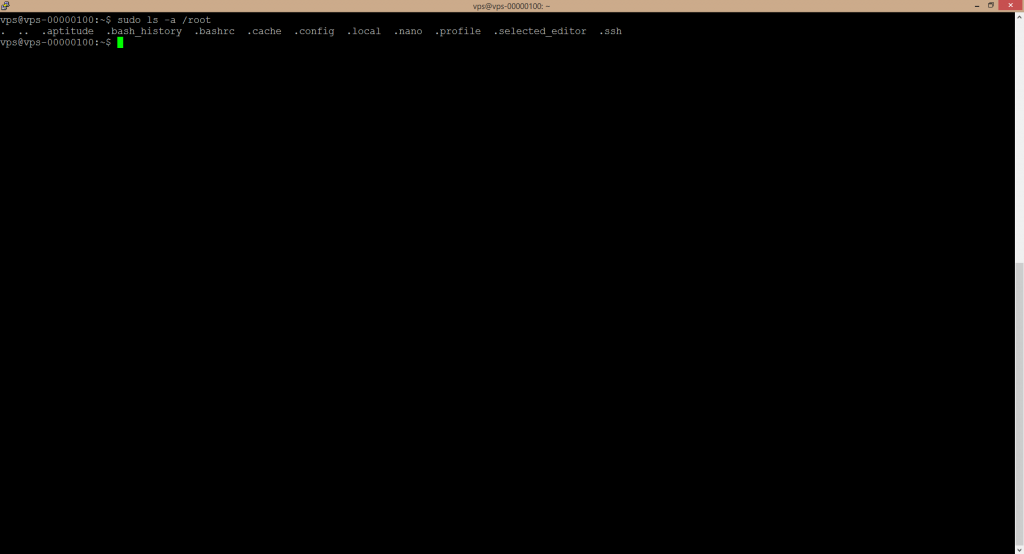
sudo ls –a /root
The ultimate goal of the sudo mechanism is to minimalize root user account usage. We follow the goal of achieving higher security and therefore have not and will not tell you the root user account password. Yet you do not need the root user account. The user account for which you have received the credentials is a sudo member. Thus you only need to put sudo before the command which requires the elevated permissions. The system will verify that the user account under which you work is a sudo member and then execute the particular command.
Certainly, it is possible to set the password for the root user account. However, it increases the probability that by using the root user account, you will allow the attackers to steal your virtual machine or service.
One thing which you could make use of at some time is the option to switch to the root user temporarily. There is no need to set the password in order to do so. If the user account under which you just operate is a sudo member, you can switch to the root user account by executing the following command:
sudo su –
Switching to the root user is indicated by the change of the way the bash prompt looks like, that is from username@hostname to root@hostname. However, when switched to the root user account, do perform only the operations for which the use of that user account is absolutely necessary. Then, you stop working under the root user account by executing the following command:
exit
Again, leaving the root user account is indicated by the change of the way the bash prompt looks like, that is from root@hostname to username@hostname.
Conclusion
Now, you are aware of the reasons for not being told the root user account password, and you know how to use the user account for which we have sent you the credentials in order to perform the operations which require elevated permissions. We recommend not to use the root user account unless it is absolutely necessary and even then just for an absolutely necessary amount of time. You should always end working under the root user account in a proper way. If necessary, it´s better to use sudo instead of the root user account.